Edition 1
Published on 12/6/2023

Welcome to the first edition of ACM Chronicles for this year! We would talk about Cryptography, Encryption, Smart Water-Bottles and so much more!
Sneak Peak Into Cryptography 👀
Cryptography, a word with Greek origins, means, “secret writing.” It is a technique of securing information and communications through codes so that only those people for whom the information is intended can understand and process it.
In simpler terms when you send a letter to someone while it is traveling to its destination the letter can be read by anyone whereas with cryptography you are sending a letter in a locked box that can be only opened by you or the person you want to send it to.
Mainly used to defend against passive security attacks. Passive security attacks are attacks where attackers aim to take data from the user hence cryptography remains important to protecting data and users, ensuring confidentiality, and preventing cyber criminals from intercepting sensitive corporate information.
To unlock your phone, you must enter a password then it compares with the one stored in it. Without cryptography, the password could be extracted from the storage of your phone and then be used to open it.
Now there are many ways and algorithms for encrypting data, but they use complex mathematical equations to make it secure. But for the sake of simplicity, we'll use the example of Caesar Cipher. It is one of the simplest and most widely known encryption techniques to start our journey in the world of encryption.

Lets Understand Caesar Cipher
The way this works is you take the text you want to encrypt and shift every letter by a fixed number (let's call it K) of letters in the alphabet. So, if your number K is 2, then A becomes C, B becomes D, C becomes E etc. and Z cycles over and becomes B. The message ATTACK, with k=3 is encrypted to DWWDFM. To decrypt, you simply shift the letters in the opposite direction! D shifted back by 3 positions becomes A, W shifted becomes T and so on...
Can You decrypt the word qsc with K=10?
In general, there are three types of cryptography:
- Symmetric Key Cryptography: It is an encryption system where the sender and receiver of a message use a single common key to encrypt and decrypt messages. Explaining with a padlock analogy would be better.
- Imagine Alice and Bob both have the same padlock and key. They have previously agreed on using this specific padlock and key for their communication. This key is their shared secret.
- If Alice wants to send a secure message to Bob, she puts her message in a box and locks it with the shared padlock using the shared key.
- When Bob receives the locked box, he uses the same shared key to unlock it, revealing the message inside.
- It is a simpler method of encryption but the problem here is how do you share the key with the other person safely without anyone else intercepting?
- Asymmetric Key Cryptography: Under this system, a pair of keys is used to encrypt and decrypt information. A receiver's public key is used for encryption and a receiver's private key is used for decryption. Public key and Private keys are different. Even if the public key is known by everyone the intended receiver can only decode it because he alone knows his private key. Similar example as above:
- Alice and Bob each have their own unique pair of a padlock (public key) and a unique key (private key).
- If Alice wants to send a secure message to Bob, she uses Bob's public padlock (key) to lock the message (encrypt it). Alice cannot unlock it once it's locked.
- When Bob receives the locked message, he uses his private key (unique key) to unlock it, revealing the message inside. Nobody else can unlock it because only Bob has the unique key that matches his padlock.
- Hashing: It is a process in which a mathematical algorithm takes an input (or 'message') and returns a fixed-length string of characters, which is typically a sequence of numbers and letters. The output, called the hash value or hash code, is unique to the specific input data. It is extremely difficult (practically impossible) to reverse the process and obtain the original input from the hash value. This property makes it useful for securely storing passwords and ensuring data integrity.
But this is also a problem as for the same input, the hash function will always produce the same hash value. This means that if two users have the same password, they will also have the same hash value. This is a security risk, as it allows attackers to find users with the same password.
To overcome this problem, salt can be added to the input before hashing. A salt is a random string of characters that is added to the input of hash functions to produce unique hash values for the same input. This makes it impossible for attackers to find users with the same password.
Understanding Quantum Cryptography 🤯
Have you ever heard of a computer that can do things regular computers can't? These special computers are called quantum computers. They are different from the computers you use at home or school because they use something called “qubits” instead of regular “bits.” A bit is like a light switch that can only be on or off, like a zero or a one. But a qubit can be both zero and one at the same time! This means quantum computers can do many things at once and work much faster than regular computers. It's like having many helpers working on a task together instead of just one. One application of it would be quantum cryptography.
Quantum cryptography isn't just another buzzword in the world of technology; it's a transformative leap into a new era of secure communication. In a world where data breaches and cyberattacks have become all too common, the need for unbreakable encryption has never been greater. That's where quantum cryptography steps in. Imagine a world where your digital secrets are truly safe, beyond the reach of even the most advanced hackers and supercomputers. This is the promise of quantum cryptography. Unlike classical encryption, which relies on mathematical algorithms, quantum cryptography leverages the strange and wondrous properties of quantum mechanics.
But how does it work?
At the heart of quantum cryptography is a concept called Quantum Key Distribution (QKD). It uses qubits as keys. These qubits have the remarkable ability to exist in multiple states simultaneously, a property known as superposition. If anyone tries to intercept or measure them, their quantum state instantly changes, revealing the intrusion. It's like having a lock that not only keeps your secrets safe but also alerts you if someone tries to tamper with it.
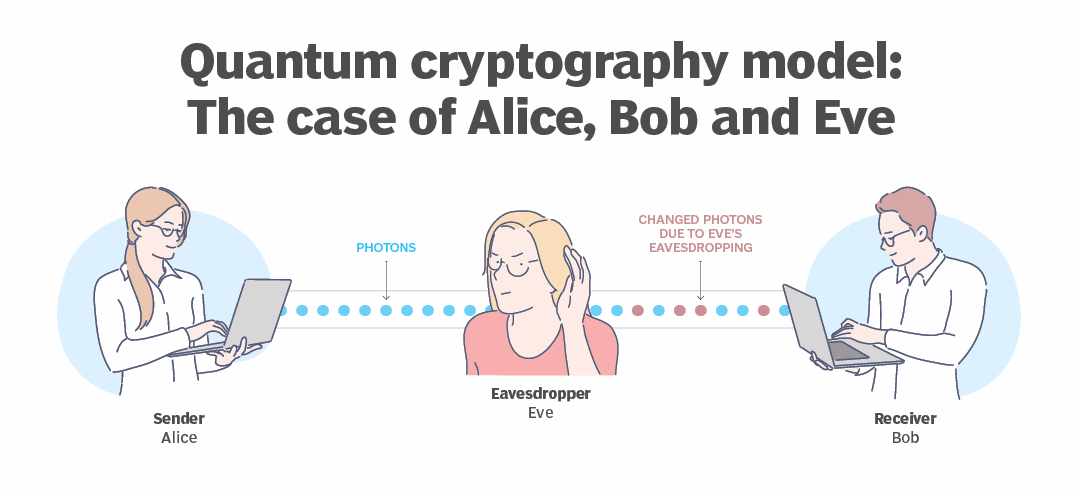
The applications of quantum cryptography are vast and transformative. It secures communication, protecting messages and data from prying eyes. It safeguards financial transactions, ensures the privacy of medical records, and even strengthens the integrity of elections. Quantum cryptography is the answer to a future where digital threats are constantly evolving, and traditional encryption methods may become vulnerable to quantum attacks.
But it's not just about security; it's about being at the forefront of a technological revolution. Quantum technology is poised to redefine industries, from computing to communication. Understanding quantum cryptography isn't just about staying safe in a digital age—it's about shaping that age, and pioneering new frontiers in science and technology.
Intriguingly, quantum cryptography isn't science fiction; it's cutting-edge reality. It's the digital fortress that empowers individuals, businesses, and governments to communicate and exchange information with unwavering confidence. So, if you're curious about the future of secure communication and want to be part of a digital revolution, quantum cryptography is your gateway to a world where secrets remain truly secret.
Next Big Idea 💡
Fluid intake monitoring is an essential component in preventing dehydration and overhydration, especially for the senior population. Numerous critical health problems are associated with poor or excessive drinking such as swelling of the brain and heart failure. Real-time systems for monitoring fluid intake will not only measure the exact amount consumed by the users but could also motivate people to maintain a healthy lifestyle by providing feedback to encourage them to hydrate regularly throughout the day. It's easy to believe that when it comes to hydration, more is always better. But that's not necessarily the case as mentioned above. To tackle this problem, we can come up with a solution for a smart water bottle.

Technical Details:
The smart bottle would have a whole slew of sensors on the bottle's bottom for accurately detecting the level of water in the bottle like an ultrasonic sensor that emits sound waves and measures the time it takes for the waves to bounce back after hitting the water surface. By calculating the time, it takes for the signal to return, you can determine the distance from the sensor to the water surface, which represents the water level in the bottle, or a weight sensor placed under the bottle can measure the change in weight as water is consumed. By tracking the weight difference, you can estimate the remaining water level!
Now the data collected is sent to a server that is owned by the bottle makers or a self-hosted approach could be provided. The data would just consist of the amount of water you have consumed, but meaningful conclusions must be made from it. This is where machine learning comes into play. A predefined ML model is initially used, based on the user's age, diseases, external environment, etc. The model is then trained on the data collected from the user and the model is updated. You can then predict the amount of water the user should consume in a day and the amount of water the user has consumed in a day. The user is notified if he is not drinking enough water.
Recommendations And Reviews 📚
roadmap.sh
It is a community effort to create roadmaps, guides, and other educational content to help guide developers in picking up a path and guiding their learning. Community-created roadmaps, guides, and articles to help developers grow in their careers. Basically, this website will show you exactly what you need to learn in the right order for the programming language you're interested in.
This is a alternate way of learning a programming language/software. This could also help in getting out of the video 'tutorial hell' where you essentially just keep following tutorials without striking out in your own and actually building something. Most learning comes from the trial and error of building an application so if you always follow a tutorial you get stuck at a basic level.
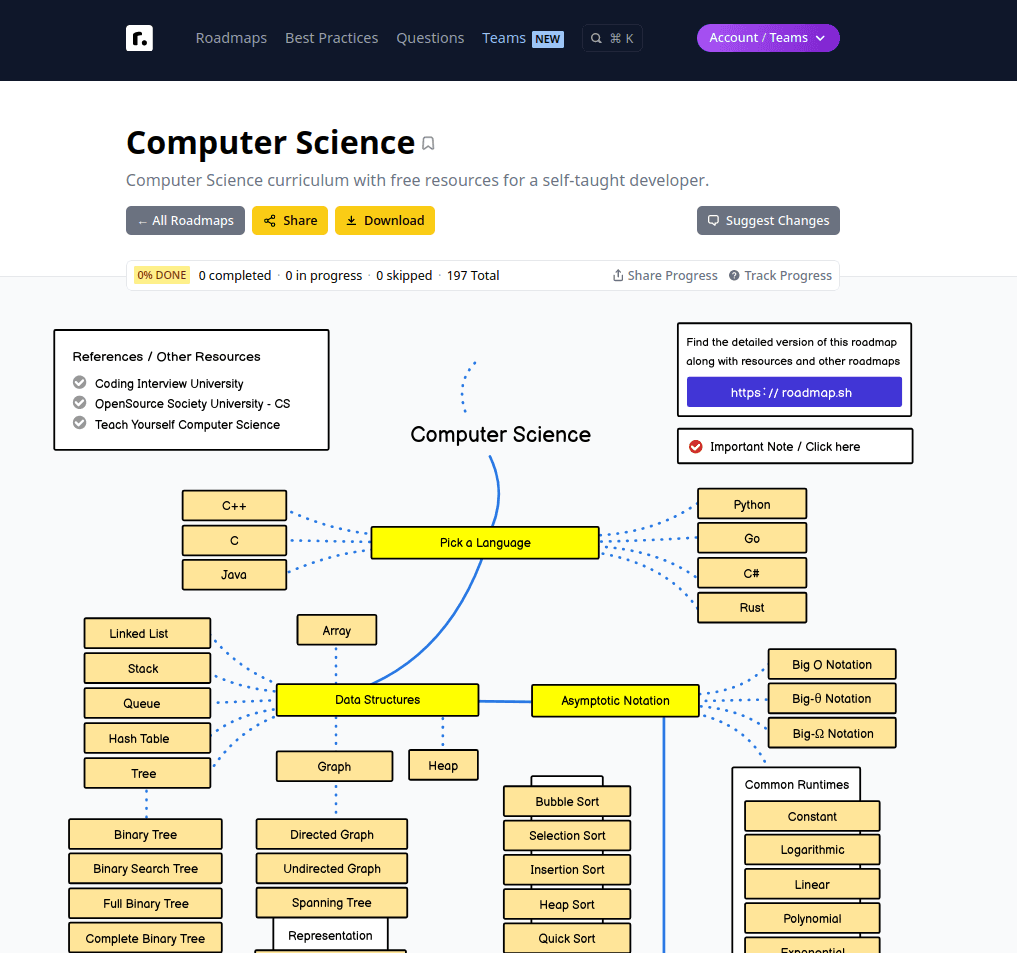
Some features of this site
- Beginner to Expert Level: The site caters to individuals at different skill levels, from beginners to experts. It provides guidance on how to progress from one level to the next in your chosen field. Each roadmap includes a detailed curriculum with various topics, subtopics, and resources for each stage of learning.
- Open Source: The project is open source, which means that users can contribute to and improve the roadmap content. This collaborative approach allows the community to keep the information up-to-date and accurate. Even you can contribute in making the roadmap for a particular language or updating a existing roadmap. Learn How to Contribute ➚
- Visual Flowcharts: One of the key features of is its visually appealing flowcharts and diagrams. These visual representations help users understand the learning paths and the sequential progression of skills and knowledge in a particular technology domain. The use of visual aids enhances the UX by making complex information more digestible.
- Other than the amazing flowcharts, textual and video guides explaining a specific topic are present
What is ACM Upto! 🤔

ACM MPSTME hosted an event called Programming For Everyone! It is a thrilling annual event from October 17th to 19th, 2023! It is a comprehensive workshop on two of the most widely used programming languages, C++ and Python. These workshops covered everything from the basics to advanced concepts, ensuring participants gained a strong foundation in both languages. What sets PFE apart is its strong sense of community. This collaborative atmosphere fostered not only technical skills but also communication and teamwork. Overall the event was greatly successful!